The Simplicity Of Paper Ballots Integrated With Un-Hackable Encryption.
SECURE.
TRANSPARENT.
ACCESSIBLE.
PROBLEM: DOES MY VOTE COUNT?
Political contention has spread from the campaign trail to the ballot box, and people are increasingly losing confidence in our election process.
Each side claims the other is cheating the system, but no one can provide conclusively indisputable proof.
Our current systems are cumbersome, all votes are not always counted (e.g., absentee ballots and military ballots). Sometimes, election outcomes are not known for weeks because a lack of confirmed chain-of-custody integrity creates space for doubt.
Secretaries of State are besieged and not equipped to provide the transparency demanded.
Is there a solution both sides can agree upon that can bring confidence and integrity back to our elections? The answer is a resounding YES!
SOLUTION: REDO VOTING. YOUR VOTE WILL ALWAYS COUNT!
The world’s first automated, completely auditable, digitally secure, large-scale voting system. Click the STARS below to learn more.
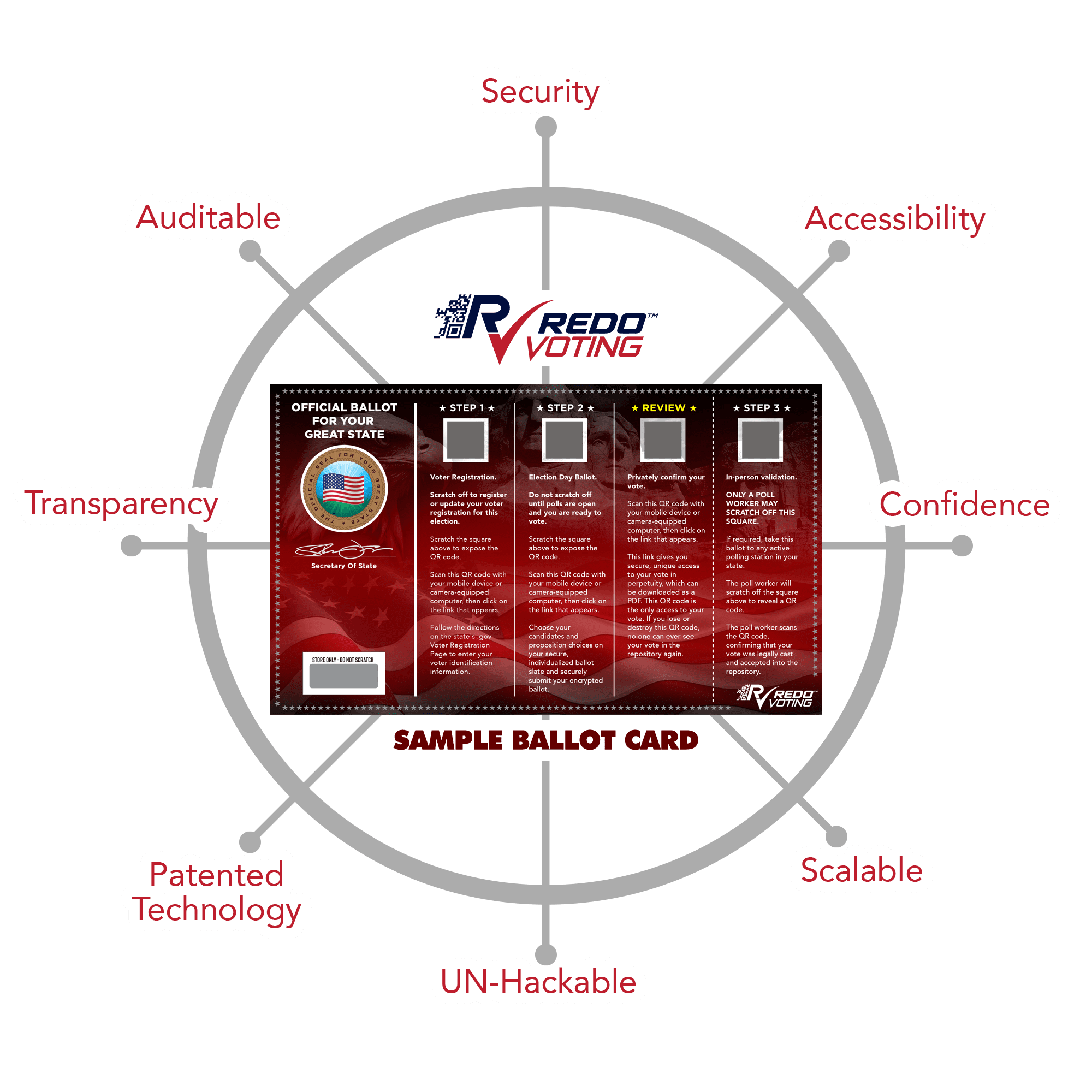
SECURITY
In the most direct terms, Redo Voting is a mashup of existing secure document technology used by state lotteries, combined with government-level encryption, resulting in a voting system that is paper based, but uses a web browser for data entry.
Our security protects privacy, ensures that voters are physically safe, protected from intimidation, harassment, or harm, and that their legitimate individual votes are delivered and tabulated as cast in a timely, accurate, and legally defined manner.
ACCESSIBILITY
Accessibility ensures that every registered voter has uncomplicated access to legally exercise their right to vote in local, state, and federal elections without unreasonable difficulty.
There are two sides to the accessibility argument. One side claims that making ballot access too easy dilutes security and allows illegitimate votes to be injected into the process. The other side claims that systematic efforts to restrict ballot access in the name of security has the effect of disenfranchising and intimidating important subsets of legitimate voters.
AUDITABLE
Redo Voting allows for third parties to audit the election in real time and to perform their own tallies of the decrypted results. This ensures full transparency and auditability, as the encrypted election data cannot be viewed without the encryption key.
Because the encryption of a voter’s individual ballot is tied directly to the QR code in their possession, seen only by their eyes, they and only they can use that QR code to confirm their vote was submitted as cast. This ensures the reliability of the system from the beginning of the process when the voter acquires their ballot access card into perpetuity, as a voter has perpetual exclusive access to their personal ballot.
CONFIDENCE
Confidence is a combination of auditability, transparency, and reliability, ensuring that there is a clearly observable, unobstructed path from the point where a vote is cast to where it is tabulated, resulting in a verified artifact from each voting transaction. Ensuring that the process for casting and tabulating votes is well understood and the rules clearly followed. Ensuring that final vote tabulation is completely trustworthy and accurate.
SCALABLE
Every Redo ballot is processed in exactly the same way as every other Redo ballot, with exactly the same security and transparency applied to each one. There is no batch processing of voter transactions. Each individually encrypted transaction moves directly from the voter to a trusted digital repository on a .gov server. Any election can be scaled from three voter transactions (only because there is really no point to an election with one or two voters) to as many voter transactions as a trusted digital repository can accommodate. With cloud computing, the size of a trusted digital repository is infinite.
UN-HACKABLE
Given enough computing power and time, theoretically, everything is hackable. However, to hack into even one voter transaction encrypted with SHA-512-bit encryption, you would need the computing power of a modern nation state and more time than the universe has been in existence to be successful.
The un-hackable claim rests on two important aspects. First, the use of QR codes for access. QR Codes cannot be hacked, but it is possible to replace a QR Code by another or to create a QR Code that will redirect to malicious content. Because distribution-controlled scratch-off ballot access cards contain QR codes that will never have been seen before they are used, that possibility drops off dramatically.
PATENTED TECHNOLOGY
Redo Voting has applied for both domestic and international patents on the Redo Voting process. The process applies two established secure technologies, SHA-2 encryption and QR codes. The SHA-2 family of algorithms are patented under U.S. patent 6829355, which is released under a royalty-free license. There are no copyright or patent restrictions on QR codes. It is the combination of these two technologies creating a secure, un-hackable multi-use tabulation platform that is patented.
TRANSPARENCY
The entire Redo Voting system is open to the public and verifiable before, during, and after an election. That is what true TRANSPARENCY looks like.
By the paper Ballot allowing data entry using a pc or mobile phone browser, we provide all browser standards for ADA and other compliance.
SOLUTION: WITH REDO VOTING, YOUR VOTE WILL COUNT!
The world’s first automated, completely auditable, digitally secure, large-scale voting system. Here is a Sample Ballot Card. Clicking on the tabs to learn more.
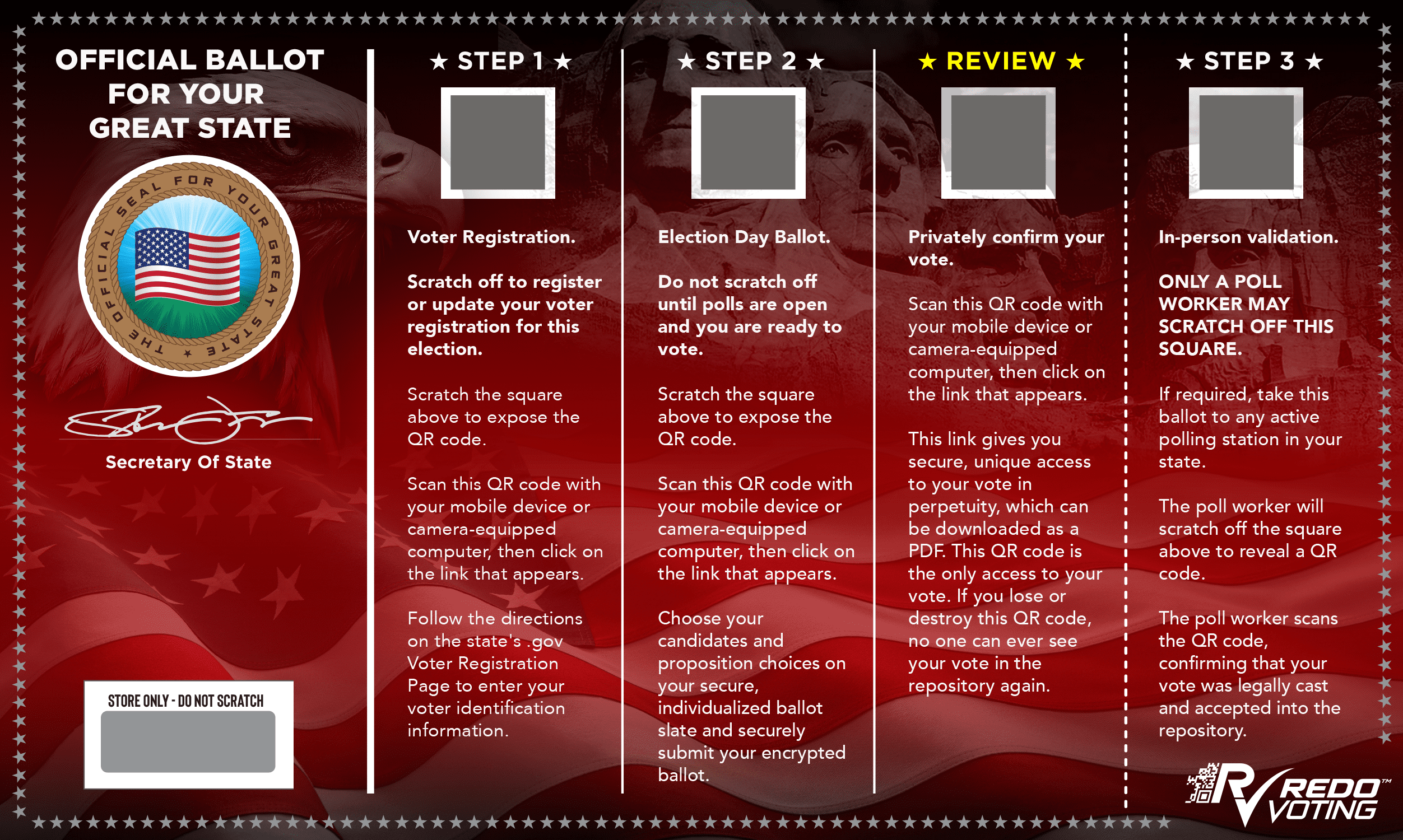
SECURITY
In the most direct terms, Redo Voting is a mashup of existing secure document technology used by state lotteries, combined with government-level encryption, resulting in a voting system that is paper based, but uses a web browser for data entry.
Our security protects privacy, ensures that voters are physically safe, protected from intimidation, harassment, or harm, and that their legitimate individual votes are delivered and tabulated as cast in a timely, accurate, and legally defined manner. CONTINUE READING
TRANSPARENCY
The entire Redo Voting system is open to the public and verifiable before, during, and after an election. That is what true TRANSPARENCY looks like.
By the paper Ballot allowing data entry using a pc or mobile phone browser, we provide all browser standards for ADA and other compliance.
PATENTED TECHNOLOGY
Redo Voting has applied for both domestic and international patents on the Redo Voting process. The process applies two established secure technologies, SHA-2 encryption and QR codes. The SHA-2 family of algorithms are patented under U.S. patent 6829355, which is released under a royalty-free license. There are no copyright or patent restrictions on QR codes. It is the combination of these two technologies creating a secure, un-hackable multi-use tabulation platform that is patented.
CONTINUE READING
AUDITABLE
Redo Voting allows for third parties to audit the election in real time and to perform their own tallies of the decrypted results. This ensures full transparency and auditability, as the encrypted election data cannot be viewed without the encryption key.
Because the encryption of a voter’s individual ballot is tied directly to the QR code in their possession, seen only by their eyes, they and only they can use that QR code to confirm their vote was submitted as cast. This ensures the reliability of the system from the beginning of the process when the voter acquires their ballot access card into perpetuity, as a voter has perpetual exclusive access to their personal ballot.
CONFIDENCE
Confidence is a combination of auditability, transparency, and reliability, ensuring that there is a clearly observable, unobstructed path from the point where a vote is cast to where it is tabulated, resulting in a verified artifact from each voting transaction. Ensuring that the process for casting and tabulating votes is well understood and the rules clearly followed. Ensuring that final vote tabulation is completely trustworthy and accurate.
SCALABLE
Every Redo ballot is processed in exactly the same way as every other Redo ballot, with exactly the same security and transparency applied to each one. There is no batch processing of voter transactions. Each individually encrypted transaction moves directly from the voter to a trusted digital repository on a .gov server. Any election can be scaled from three voter transactions (only because there is really no point to an election with one or two voters) to as many voter transactions as a trusted digital repository can accommodate. With cloud computing, the size of a trusted digital repository is infinite.
ACCESSIBILITY
Accessibility ensures that every registered voter has uncomplicated access to legally exercise their right to vote in local, state, and federal elections without unreasonable difficulty.
There are two sides to the accessibility argument. One side claims that making ballot access too easy dilutes security and allows illegitimate votes to be injected into the process. The other side claims that systematic efforts to restrict ballot access in the name of security has the effect of disenfranchising and intimidating important subsets of legitimate voters. CONTINUE READING
UN-HACKABLE
Given enough computing power and time, theoretically, everything is hackable. However, to hack into even one voter transaction encrypted with SHA-512-bit encryption, you would need the computing power of a modern nation state and more time than the universe has been in existence to be successful.
The un-hackable claim rests on two important aspects. First, the use of QR codes for access. QR Codes cannot be hacked, but it is possible to replace a QR Code by another or to create a QR Code that will redirect to malicious content. Because distribution-controlled scratch-off ballot access cards contain QR codes that will never have been seen before they are used, that possibility drops off dramatically. CONTINUE READING
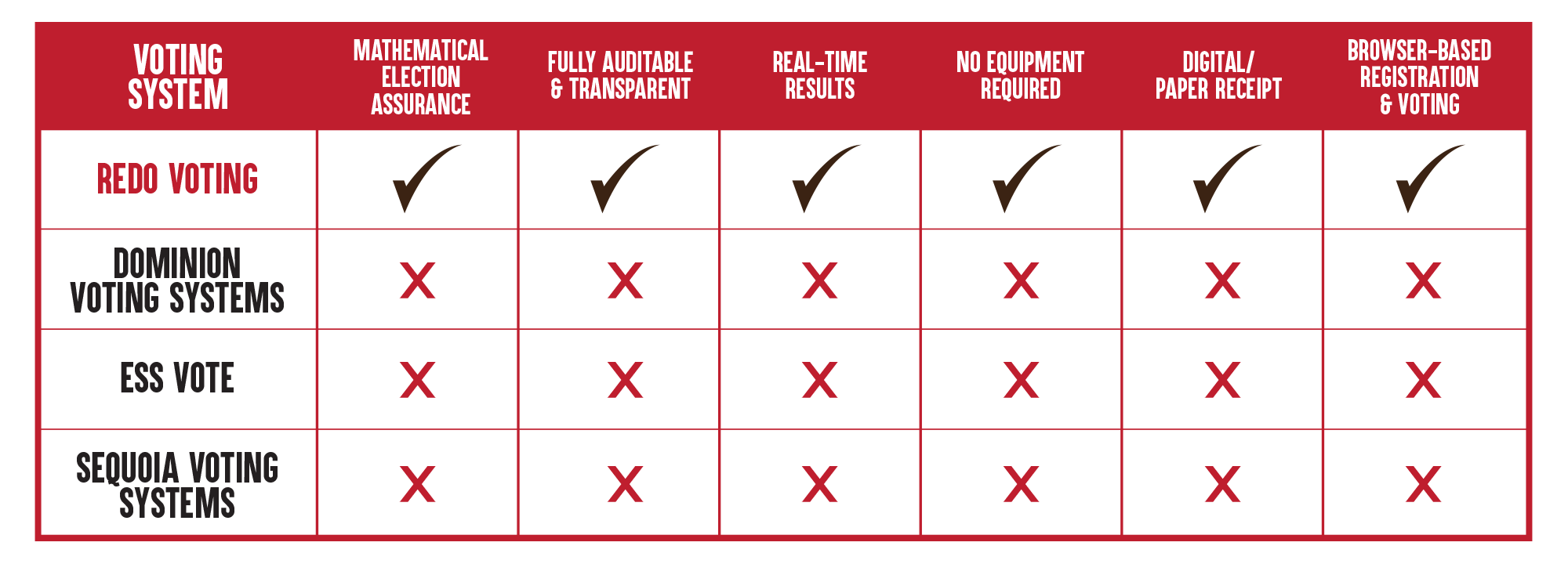
VOTING SYSTEM COMPARISON
REDO VOTING is the first fully automated, completely auditable, digitally secure, large-scale voting system in the world. It combines modern digital cryptography and data management technologies with secure paper documents/ballots to ensure an end-to-end, unbreakable chain-of-custody
REDO VOTING reduces the need for early voting, eliminates delays in tabulation, and allows for legal ballots (including absentee / military ballots) to be cast in real-time via a secure browser.
It detects and stops irregularities, is forensically auditable, and produces accurate results, all in real-time.
REDO VOTING provides 100% mathematical validation of every ballot.
THE ONLY WAY TO SECURE OUR VOTING PROCESS
Current processes cannot compare to REDO VOTING’s process security.

Hand-Fed Ballots
See that paper ballot being hand-fed into that machine? That is a problem. It is not a secure document and has no chain-of-custody. There is no way to determine whether or not it is a legitimate vote in an initial tally or hand recount.

Absentee Ballots
Absentee balloting is just as fallible. The number of envelopes around the vote is irrelevant if there is no observable, confirmed chain-of-custody. You should be sent a ballot that is YOURS, and your vote should be submitted as a secure document protected from tampering and misallocation.

Securely Printed
REDO VOTING ballots are printed by the same professionals that state lotteries have relied upon for 30 years to print $80 BILLION in tickets each year. If there was a way to hack this system, it would have happened by now.

Securely Delivered
Securely delivered by the same professionals that state lotteries rely upon to deliver BILLIONS of state lottery tickets each year. Every ballot is digitally tracked from the printer, right up to when you cast your vote.
REDO VOTING’s ballot is cryptographically assigned to YOU and only you. It is digitally tracked from the printer to the place you pick it up, and issued to you as a secure document with the same digital identification check used for purchasing cigarettes or alcohol. No one but you can use your registration because you establish a private, four-digit access PIN when you pick up your ballot. Additionally, no person or computer program can EVER connect you to your vote once cast because one-way encryption disassociates your identity from your ballot. The system only knows that your vote is cast from a legitimate registration, and it goes directly to your state’s repository.
FREQUENTLY ASKED QUESTIONS
Tom Flanigan of NPR Interviews Founder & President of REDO VOTING, John Rogers